Computer network and IT Security professionals know the furious discussion going on about the last NSS lab report. This report is about the recent experiment they have conducted with popular security products. They tested different security products in 6 different situations and one of them "TCP Split Handshake Attack" was very successful for most of the products they have tested. They successfully breached the security of most of the Firewall products from different vendors using TCP Split Handshake Attack method. So what is TCP Split Handshake Attack? How it is a threat for current network? If we refer RFC 793 we can see how a TCP connection is established. TCP (Transmission Control Protocol) is a connection-oriented protocol and thus it needs a handshaking process to establish a successful connection. Diagram provided below explains the working of a handshake process.
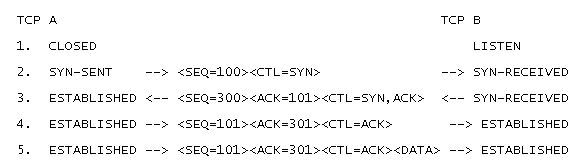
Before we go to Transmission Control Protocol Split Handshake, we should understand the process of three-way handshake to establish a connection. Consider a scenario where we have Two TCP devices A and B. Here A wants to start a TCP connection with B and so A acts as client and B acts as a server. In TCP connection the SYN\ACK packet is determining the server and client. So a proper TCP handshake is necessary to establish the correct server client relation. A simplified version of this process between A and B is given below.
Client (A) ISN =X
Server (B) ISN =Y
ISN= Initial Sequence Number
Step 1: A --- (connection request)-->B SYN=1, Seq= X
Step 2: B --- (Connection Granted) -->A SYN=1, Seq=Y, ACK= X+1
Step 3: A ----(acknowledgment) -->B SYN=0, Seq= X+1, ACK= Y+1
Now let us check how it occurs. The above three-way handshake method can be written as below.
Step 1: A ----->B SYN, Seq= X
Step 2: B ----->A ACK sequence number of A is X
Step 3: B -----> A SYN, the Sequence number of B is Y
Step 4: A ---> SYN\ACK Sequence number of A is X, the Sequence number of B is Y+1 ( This is a possible error in many vendor products )
Step 5: Again the Three-way handshake continues and the server will be A and B will be a client. This process confuses the firewall.
The above error in three-way handshake leads to TCP Split Handshake Attack where Firewall will be confused to find the actual server and client. As a result, firewall thinks like B is the client (where in reality A is the client and requested connection) and it may lead to a security vulnerability. In this split signals, some products (where the signal is strange ) drop the entire connection but some respond to it in unexpected ways.

What is TCP Handshake?
Before we go to Transmission Control Protocol Split Handshake, we should understand the process of three-way handshake to establish a connection. Consider a scenario where we have Two TCP devices A and B. Here A wants to start a TCP connection with B and so A acts as client and B acts as a server. In TCP connection the SYN\ACK packet is determining the server and client. So a proper TCP handshake is necessary to establish the correct server client relation. A simplified version of this process between A and B is given below.
Client (A) ISN =X
Server (B) ISN =Y
ISN= Initial Sequence Number
Step 1: A --- (connection request)-->B SYN=1, Seq= X
Step 2: B --- (Connection Granted) -->A SYN=1, Seq=Y, ACK= X+1
Step 3: A ----(acknowledgment) -->B SYN=0, Seq= X+1, ACK= Y+1
What is TCP Split Handshake
Now let us check how it occurs. The above three-way handshake method can be written as below.
Step 1: A ----->B SYN, Seq= X
Step 2: B ----->A ACK sequence number of A is X
Step 3: B -----> A SYN, the Sequence number of B is Y
Step 4: A ---> SYN\ACK Sequence number of A is X, the Sequence number of B is Y+1 ( This is a possible error in many vendor products )
Step 5: Again the Three-way handshake continues and the server will be A and B will be a client. This process confuses the firewall.
The above error in three-way handshake leads to TCP Split Handshake Attack where Firewall will be confused to find the actual server and client. As a result, firewall thinks like B is the client (where in reality A is the client and requested connection) and it may lead to a security vulnerability. In this split signals, some products (where the signal is strange ) drop the entire connection but some respond to it in unexpected ways.
Related Articles
- Denial of Service attack (DOS)
- What is Smurf attack and How to prevent it
- How to Increase the Speed of Internet Connection
- How to Check Transmission Control Protocol Connection